一、该问题的重现步骤是什么?
1. 系统被检测出SQL注入漏洞,使用框架bladex-boot2.9.1,下载blade-tool2.9.1安装到本地仓库,导入项目后重新编译访问
2. https://xxxxxx.com/api/blade-user/export-user?Blade-Auth=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJpc3MiOiJpc3N1c2VyIiwiYXVkIjoiYXVkaWVuY2UiLCJ0ZW5hbnRfaWQiOiIwMDAwMDAiLCJyb2xlX25hbWUiOiJhZG1pbmlzdHJhdG9yIiwicG9zdF9pZCI6IjExMjM1OTg4MTc3Mzg2NzUyMDEiLCJ1c2VyX2lkIjoiMTEyMzU5ODgyMTczODY3NTIwMSIsInJvbGVfaWQiOiIxMTIzNTk4ODE2NzM4Njc1MjAxIiwidXNlcl9uYW1lIjoic3VwZXJfYWRtaW4iLCJuaWNrX25hbWUiOiLnrqHnkIblkZgiLCJkZXRhaWwiOnsidHlwZSI6IndlYiJ9LCJ0b2tlbl90eXBlIjoiYWNjZXNzX3Rva2VuIiwiZGVwdF9pZCI6IjIyNyIsImFjY291bnQiOiJzdXBlcl9hZG1pbiIsImNsaWVudF9pZCI6InNhYmVyIiwiZXhwIjoxNzE2NzEyNzU0LCJuYmYiOjE3MTY1Mzk5NTR9.9DQdUSbRa2AJC7cNV9Mvfn7-3TJVtBb6DuUpkon1LBY&account=undefined&realName=undefined&updatexml(1,concat(0x7e,user(),0x7e,1)=1)
3.
二、你期待的结果是什么?实际看到的又是什么?
期待结果:接口请求返回结果不应该暴露数据库字段。
实际结果:{
"code": 500,
"success": false,
"data": null,
"msg": "nested exception is org.apache.ibatis.exceptions.PersistenceException: \n### Error querying database. Cause: com.baomidou.mybatisplus.core.exceptions.MybatisPlusException: Failed to process, Error SQL: SELECT id, tenant_id, user_type, account, name, real_name, email, phone, birthday, role_id, dept_id, post_id FROM blade_user WHERE (real_name LIKE ? AND (1,concat(0x7e,user(),0x7e,1) LIKE ? AND account LIKE ? AND is_deleted = ?)\n### Cause: com.baomidou.mybatisplus.core.exceptions.MybatisPlusException: Failed to process, Error SQL: SELECT id, tenant_id, user_type, account, name, real_name, email, phone, birthday, role_id, dept_id, post_id FROM blade_user WHERE (real_name LIKE ? AND (1,concat(0x7e,user(),0x7e,1) LIKE ? AND account LIKE ? AND is_deleted = ?)"
}
三、你正在使用的是什么产品,什么版本?在什么操作系统上?
产品:bladex-boot2.9.1
版本:2.9.1
操作系统:CentOS7
四、请提供详细的错误堆栈信息,这很重要。
五、若有更多详细信息,请在下面提供。
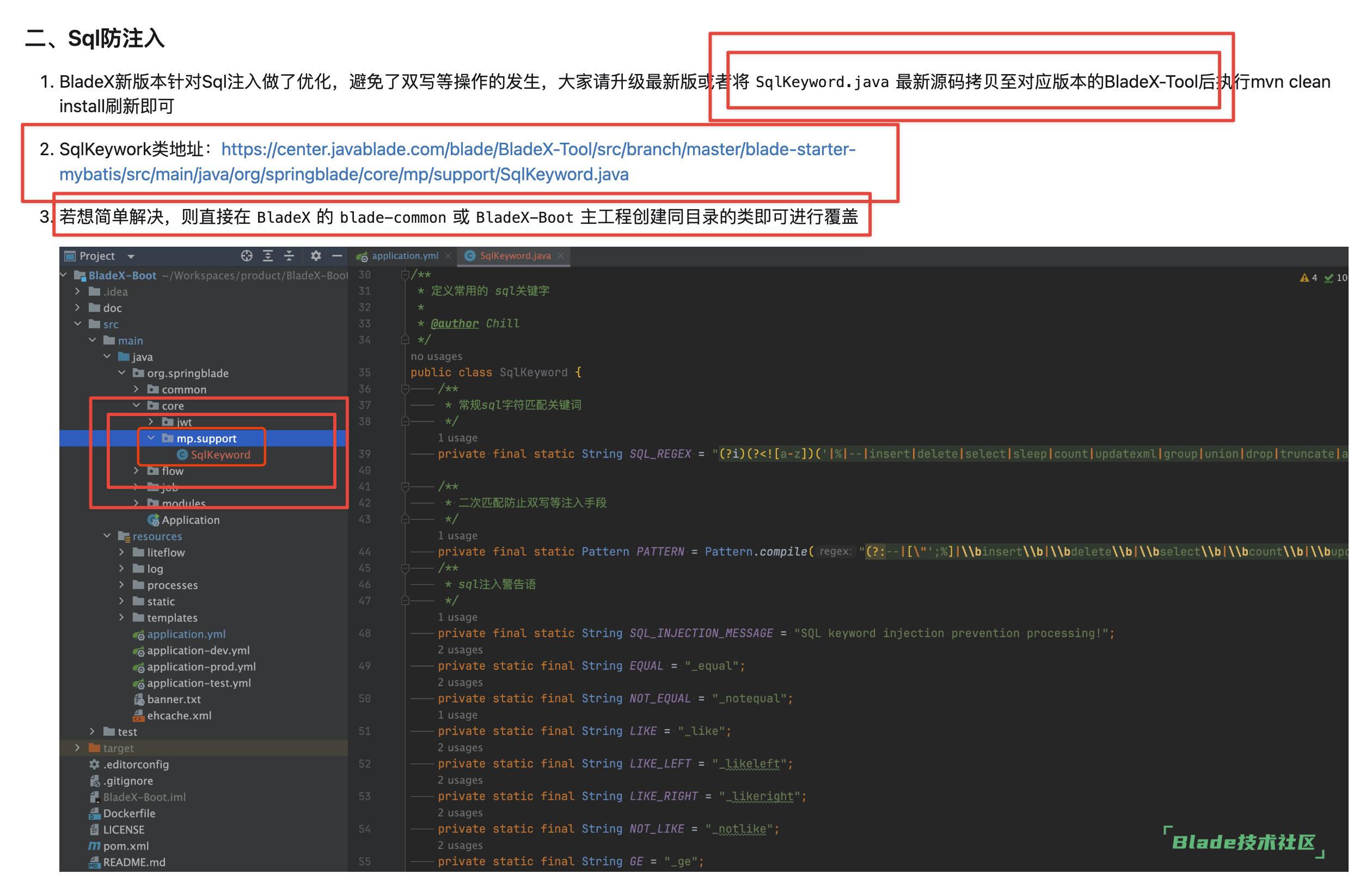
仔细看文档, 每一章节都看一遍:https://center.javablade.com/blade/BladeX-Safety
确保把最新版本替换好,然后打断点看结果,新版本的代码就不可能会返回括号等这类特殊字符
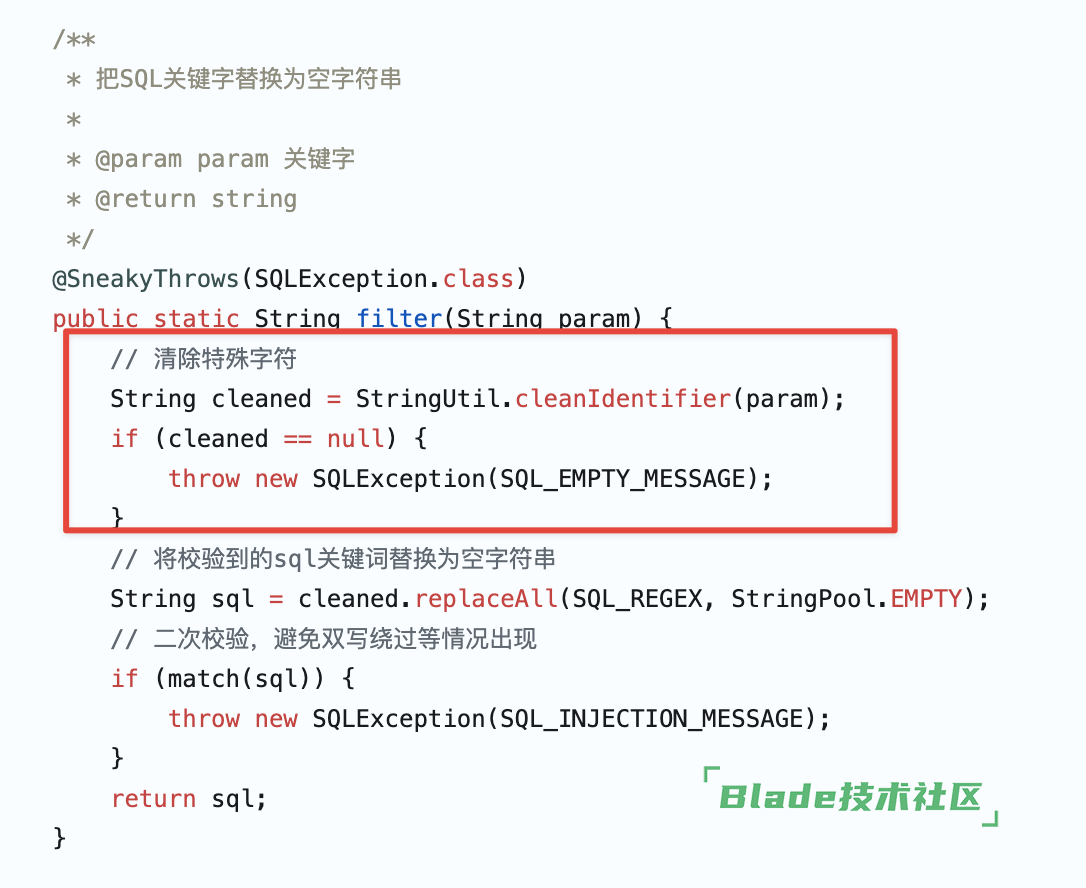
请问这个结果算不算正常?updatexml那些变成了1concat0x7e1111110x7e1
{"code":500,"success":false,"data":{},"msg":"nested exception is org.apache.ibatis.exceptions.PersistenceException: \r\n### Error querying database. Cause: com.baomidou.mybatisplus.core.exceptions.MybatisPlusException: Failed to process, Error SQL: SELECT id, tenant_id, user_type, account, name, real_name, email, phone, birthday, role_id, dept_id, post_id FROM blade_user WHERE (real_name LIKE ? AND 1concat0x7e1111110x7e1 LIKE ? AND account LIKE ? AND is_deleted = ?)\r\n### Cause: com.baomidou.mybatisplus.core.exceptions.MybatisPlusException: Failed to process, Error SQL: SELECT id, tenant_id, user_type, account, name, real_name, email, phone, birthday, role_id, dept_id, post_id FROM blade_user WHERE (real_name LIKE ? AND 1concat0x7e1111110x7e1 LIKE ? AND account LIKE ? AND is_deleted = ?)"}
正常了,注入的语句变成了一个普通字符串。
另外如果想屏蔽这个详细的报错信息,再看一下文档的第七点,可以屏蔽掉sql报错信息

扫一扫访问 Blade技术社区 移动端